Critical Flaws in Microsoft Defender for Endpoint Threaten Incident Response
A recent analysis by InfoGuard Labs has exposed severe vulnerabilities in the network communication between Microsoft Defender for Endpoint (DFE) and its cloud services. These critical flaws could allow post-breach attackers to bypass authentication, spoof data, access sensitive configuration details, and even upload malicious files to investigation packages, potentially undermining incident response efforts.
Azure Upload
The core issues lie in how the DFE agent handles requests for commands and actions.
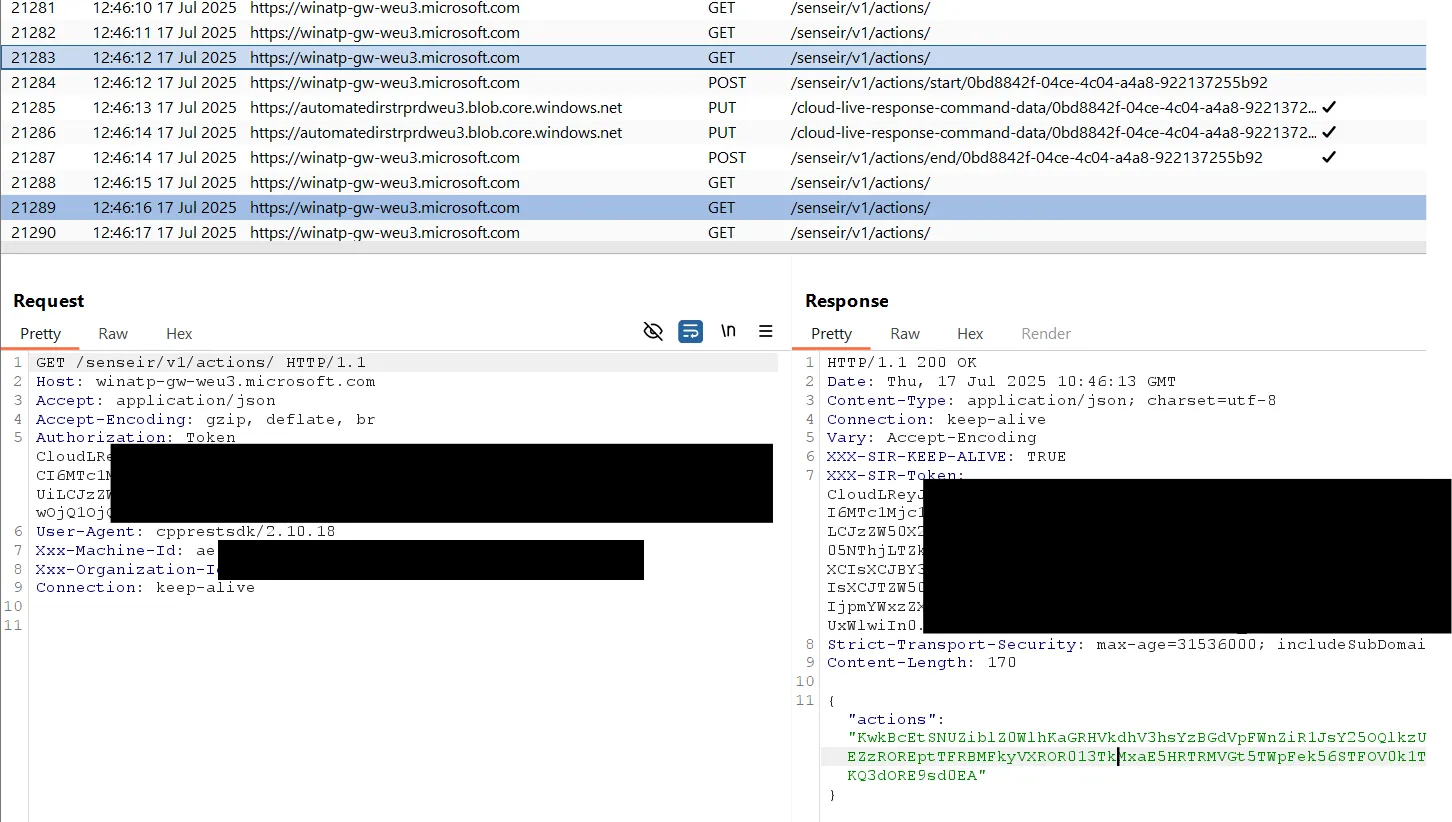
· Ignoring Authorization: The DFE agent polls a command and control endpoint for actions like device isolation or scans. Although these requests include Authorization tokens and Msadeviceticket headers, the cloud backend reportedly ignores them entirely.
· Easy Impersonation: An attacker can easily obtain the necessary machine ID and tenant ID from the system registry, which is accessible to low-privileged users. Using these IDs, an intruder can impersonate the legitimate agent and continuously query the command endpoint, snatching available commands before the DFE agent can receive them.
· Spoofing Responses: This interception allows the attacker to spoof responses. For example, they could fake an "Already isolated" status for an isolation command. This leaves the device unisolated while the Microsoft Defender Portal falsely reports the device as secured.
· Live Response and Automated Investigations: A similar vulnerability affects endpoints for Live Response and Automated Investigations , where CloudLR tokens are also ignored. Attackers can decode action payloads and use provided Azure Blob URIs with long-valid SAS tokens to upload fabricated data.
The unauthenticated access also creates significant information disclosure risks and opportunities for targeted attacks against security analysts.
· Configuration Dump: Simply polling the command endpoint without any credentials can yield an 8MB configuration dump. While not tenant-specific, this data includes detailed information like RegistryMonitoringConfiguration and ASR rules, which is highly valuable for attackers looking to evade DFE detection logic.
· Malicious File Uploads: For ongoing investigations, DFE creates investigation packages on the filesystem that are readable by any user. By exploiting the spoofing capabilities, attackers can upload malicious files with innocuous names into these packages. This is particularly alarming as it could trick security analysts into executing the malicious file during a review of the investigation data.
The research, which builds on prior EDR attack surface explorations, involved intercepting traffic using Burp Suite. InfoGuard Labs successfully bypassed certificate pinning—a common security measure—by applying memory patches to the function to always return a valid result. This enabled the plaintext inspection of HTTPS traffic between the DFE agent and the cloud.
The vulnerabilities were reported to Microsoft’s Security Response Center (MSRC) in July 2025 but were deemed low severity, with no confirmed fixes as of October 2025. InfoGuard Labs urges a higher priority for remediation, arguing that the risks of post-breach disruption and analyst-targeted attacks merit a more urgent response than MSRC’s current assessment.